Many providers offer inexpensive SSL certificates for domain-only validation. GoDaddy seems to be a popular choice given just how inexpensive the certificates are. GoDaddy’s inexpensive cert is called Standard SSL certificate.
Before we dive in, let’s recap the certificate story in Windows Small Business Server 2008. There are two "types” of certificates and four “states” your certificate can be in. Those are defined on TechNet in the Managing Certificates section of the SBS documentation. The two types are “Self-Issued” or “Trusted”, and by default, SBS 2008 ships using a self-issued certificate infrastructure, which is used to authenticate the server to the client, and encrypt the traffic between the remote client and the server. The obvious downside here is there is extra work with the certificate installer package on your remote/non-domain joined clients, and Windows Mobile devices. At some point there are enough of these to warrant the low cost to upgrade to a 3rd party Trusted certificate. With a 3rd party trusted certificate, the client computers and mobile devices already trust the root of the 3rd party certificate, as these are maintained by Microsoft Update (and various other solutions for non-Microsoft based clients/devices).
As you probably read when you learned about the Internet Address Management Wizard, we have a number of domain name providers, eNomCentral, GoDaddy, and Register.com. All three of these providers are very well equipped to sell you and facilitate installing a trusted certificate for your small business network, so feel free to shop around!
I’ll be going through the steps for GoDaddy today as they are the only provider that requires intermediate certificates, which is a bit more challenging. The process is the same for all the providers, except for eNomCentral and Register.com, you can skip the intermediate certificate steps, and naturally the UI would be different. On a final note, I have not had luck with the GoDaddy certificate and Windows Mobile 5 (Update Below), if you have Windows Mobile 5 devices, you may want to consider one of the other partners, but the best thing to do here is open the certificate store on your WM5 device and validate the root cert for the provider you’re going with is available in the certificate store.
While Matt Williamson’s Installing GoDaddy SLL Certificates on IIS7 talks generically how to install the GoDaddy SSL certificates, it isn’t detailed enough for SBS 2008. The steps below should provide detailed steps, specific for SBS 2008:
- In your Windows SBS Console on the server, navigate to the Network tab and the Connectivity sub-tab and launch the Add a Trusted Certificate connectivity task
- Click Next on the welcome screen and choose I want to buy a certificate from a certificate provider and click Next.
- Verify this information is correct. This information will be encoded in the request to the certificate provider, and cannot be changed without buying a new certificate. Additionally for some certificate requests this information could be used to contact you to validate the ownership of the domain name. Then click Next.
- Once you get to the screen below, you are now going to deal with only the certificate provider, with the encoded certificate request shown in the gray box. Since most providers have you paste this into a web browser, you should click the Copy button to place this into your clipboard.
- IMPORTANT: It’s important not to click back or next-back on this page, as it will re-generate a new encoded string, which will not match the request you make to your cert provider.
- Once the encoded string is copied safely (I paste it into Notepad so I don’t loose it during the process) Let’s close the Trusted Certificate wizard for now to get it out of the way and prevent errors now that we have that encoded text in the clipboard (and hopefully in Notepad). Let’s click Next and then select My certificate provider needs more time to process the request, and click Next again, the wizard will show a warning that it could not import the certificate into Remote Web Workplace.
- You will also notice after you click Finish, that the console now shows Request Submitted and you have an option to Remove this Certificate, which we don’t want to do unless we want to go back to the beginning.
- At this point, go to your providers website and follow the instructions for purchasing a certificate. The provider will most likely ask you to purchase the certificate before they collect the certificate information (encoded text above) from you. Notes:
- The provider may try to sell you other services, feel free to browse, but the server doesn’t require additional services
- The server does not require a wildcard certificate, port numbers (such as 987) are used to save you the cost of purchasing a wildcard certificate
- You should get a confirmation email with instructions on how to install the certificate. My particular email has this section in it, stating to log into the website to obtain my cert:
- Once I log into my account, It’s abundantly clear that I have a certificate set up waiting for me:
- I log in to my account using the ID and choose to use your certificate credit
- Next you will want to go to the Manage Certificate Control Panel:
- In the control panel, select your certificate credit and click Request Certificate
- Now you are prompted to insert the CSR, or Certificate Signing Request, which is all of the information you copied out of the trusted certificate wizard (and put into Notepad right?)
- IMPORTANT: Make sure you select the server software to be Microsoft IIS.
- Note: the actual domain name you are requesting for is encoded in the string from within the Trusted Certificate wizard
- Validate the information in the cert is correct, once you confirm it, it’ll cost more money to do this over again, and then click Confirm.
- Once you confirm, an email gets sent to the email account on file for that domain name, once you get that email, there is a verification link inside that email that needs to be clicked. Click it and approve the request, some more email will come into that account you just checked. One to tell you that it was approved, and one to give you the link to go and get the encoded text.
- One thing to note here is there are two things to download, the signed certificate itself, and the intermediate certificates which must also be installed on the website.
- Validate the install type is IIS and click Continue, then proceed to the Download Signed Certificate link and save the certificate to the desktop of the server.
- Then click the IIS Installation Instructions link to open up the installation instructions. It’s important to use these instructions for installing the Intermediate Certificate Bundle. You can follow the Installing the SSL certificate steps as well, but it will change the flow through the Trusted Certificate wizard shown later in this instruction set.
- So follow the steps from GoDaddy.com, but I’m going to paste and modify them for SBS 2008 here for you as well… These are of course subject to change without notification!!!
- Select Run from the start menu; then type mmc to start the Microsoft Management Console (MMC). Agree to the UAC prompt
- In the Management Console, select File; then "Add/Remove Snap In."
- In the Add Standalone Snap-in dialog, choose Certificates; then click the Add button.
- Choose Computer Account; then click Next and Finish.
- Close the Add Standalone Snap-in dialog and click OK on the Add/Remove Snap-in dialog to return to the main MMC window.
- If necessary, click the + icon to expand the Certificates folder so that the Intermediate Certification Authorities folder is visible.
- Right-click on Intermediate Certification Authorities and choose All Tasks; then click Import.
- Follow the wizard prompts to complete the installation procedure.
- Click Browse to locate the certificate file (gd_iis_intermediates.p7b). You’ll have to change the file filter at the bottom right to PKCS #7 Certificates.
- Choose Place all certificates in the following store; then use the Browse function to locate Intermediate Certification Authorities. Click Next.
- Click Finish.
- So follow the steps from GoDaddy.com, but I’m going to paste and modify them for SBS 2008 here for you as well… These are of course subject to change without notification!!!
- Once this is imported, we can go back to the Trusted Certificate wizard in the product
- Click Add a Trusted Certificate in the console to re-launch the wizard if you closed it (as recommended above), and click Next on the welcome page.
- Click I have a certificate from my certificate provider and click Next.
- Since GoDaddy provided me with a file, I’m going to browse to the file (alternatively if the provider gave back encoded text, that could be pasted into the wizard too) that matches my domain name, in this case, remote.seandaniel.net. and clicking Next.
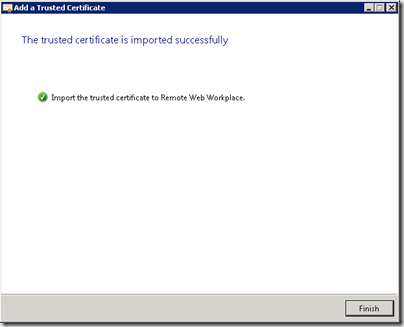
- We’re finally done, click Finished! Now remote clients will get the benefit of a trusted certificate, and the console reports Trusted as the certificate type.
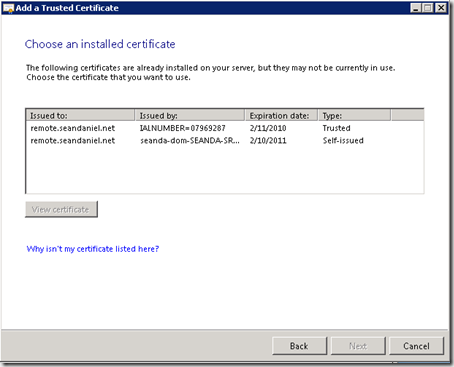
It’s important to use the Trusted Certificate wizard for the last step, to ensure that the certificate is bound to the correct IIS website, as well as TSGateway for remote desktop access. If you followed all the steps from GoDaddy to install the certificate, simply run the Trusted Certificate wizard and choose I want to replace the existing certificate with a new one, and you’ll get shown the trusted certificate and the self-issued certificate for your domain name, just choose the appropriate one based on the type and the expiration date:
On a final note, renewing your certificate after the year, just click that Add a Trusted Certificate link in the console but this time through choose I want to renew my current trusted certificate with the same provider, and follow the instructions!
I did want to call out that NetoMeter.com has a 4-step video process on how to do add GoDaddy SSL certificates to your SBS 2008 server, but a $30 monthly subscription is required to view it, which might be worth it depending on how much help you need with your SBS 2008 server, or might not be worth it if this is your only challenge.
Update – Windows Mobile 5
GoDaddy has e-mailed me regarding support for Windows Mobile 5 devices. WM5 devices older than the AKU2 update only need to have this patch installed. If it is an older WM5 device it needs to be unlocked to allow certificate installation. Once you meet all of these criteria, GoDaddy has provided steps to install the required certificates on your Windows Mobile 5 device. I will copy them here for convenience, although as a reminder, always check with GoDaddy for the latest steps!!
To install the root certificate on your Windows Mobile 5 device:
- Download the root certificate to your PC in DER format with a .cer file extension (i.e., valicert_class2_root.cer"). The root can be downloaded from the Go Daddy repository.
- Copy the downloaded root certificate to your device using ActiveSync.
- On your mobile device, locate the imported file using File Explorer and click on it.
- The device will display the following prompt: "You are about to install valicert_class2_root.cer certificate issued by http://www.valicert.com/. Do you want to continue?" (If you saved the root under a different name, that file name will show up in the prompt.)
- Accept the prompt to install the root certificate on your device.






69 comments:
What about installing UCC/SAN Godaddy Certificates for SBS 2008? Without these certs, rpc over http will not function correctly.
RPC over HTTP worked fine for me over this certificate. Why do you need a UCC/SAN certificate?
Regarding the SAN Certificate functioning correctly, this link is from the Exchange Team:
http://msexchangeteam.com/archive/2007/07/02/445698.aspx
There are two things here
(1) Autodiscovery - SBS uses a SRV record to update to remote.server.com (thus the no need for an additional SSL cert. I have a blog post here on that.
(2) the SMTP Cert - We use a self-issued cert for Exchange SMTP. Since Exchange doesn't validate if it's a trusted cert, we never replace this one.
great post. have a couple of questions:
1. if you plan on installing sbs 2008 premium, and planned to have
www.companya.com
crm.companya.com
moss.companya.com
email
exchange sync to a pda, would you go for a wildcard
If you want all of those websites to have a trusted certificate, yes, you would need a wildcard, but they are all at companya.com, why not just use the same URL?
although at the same url, was thinking about that the exchange was on the primary server as well as remote.companya.com; while crm, etc on the win2k8 box; wss vs. moss? don't know yet;
I desire the cheapest and easiest solution - thoughts?
Creating your own self-issued cert would be the cheapest by money, most expensive by time
Overloading a single use cert costs some money, and some time.
Getting a wildcard cert will be the shortest time involvement, but it's the most costly by money.
the wildcard cert from godaddy is definitely the cheapest as compared to enom or register.com - based upon your instructions above, is it more complex to apply?
The only difference is GoDaddy has extra steps to install an intermediate certificate... and the UI will be different of course, but it shouldn't be any more difficult to use any cert provider.
You can also get a UCC/SAN Certificate from www.certificatesforexchange.com at a cheap price. You can cover 5 domains for $60ish/year. If you need more, you can add them in 5 domain increments, IE: 10 or 15 and the price goes up accordingly.
I have the certificate installed from Godaddy, but I cannot bind it in the wizard. I had the certificate issued from exchange, and did it in a similar way to the Server 2008 and Exchange. I have multiple names, (autodiscover.domain.com, remote.domain.com, exchange.domain.com) according to the goddady support.
Should I revoke that certificate, delete it, and have a new one issued with jsut the remote.domain.com? Or is there a way to get it to bind to the remote site. It seems without using the wizard it is impossible.
Just one other thought, I did the binding throught he exchange management shell, but ecieved the mnessage that the certificate alreadt installed would be the default certificate, And when I use the method of the console to try to import an existing certificate, it does not show up in my list of available certificates. There are 2 certificates that were issued by the SBS, but none listed there by starfield (godaddy).
Also, In the console it says I am using a trusted certificate, and the details are the one from strafield (godaddy). But I know it is not the one bound to the remote site.
When I use the Exchange management shell, this is the error I get:
[PS] C:\Documents and Settings\oscar.meyer>
Enable-ExchangeCertificate -ThumbPrint [XXXXX-THUMBPRINT-XXXXXX] -Services "SMTP, IMAP, POP, IIS"
WARNING: This certificate will not be used for external TLS connections with an
FQDN of 'remote.domainname.com' because the self-signed certificate with
thumbprint 'AAA-THUMBPRINT-AAAAAAA' takes precedence. The
following connectors match that FQDN: Windows SBS Internet Receive SBS2008
Any thoughtson how to either overwrite or move this down the list of precedence?
There is absolutely no need to replace the Exchange certificate. Please don't bother doing this. Exchange certificates being self issued do not affect any functionality what-so-ever. So just use our trusted certificate wizard and you won't go a-stray.
Thanks for the reply Sean. I have used the wizard, and it does not seem to replace the self-issued certificate in order of preference. Is there a way to do this? Move the self-issued certificate down the list and elevate the trusted third party certificate. Both seem to co-exist, but my mobile devices with Windows Mobile will not sync correctly with the self-issued certificate. They did sync correctly in the past with the third-party trusted certificate.
Thanks again for the reply and help.
In the wizard it doesn't matter on the order, there can only be on installed on the website, so select that one and go ahead and install it. It should replace any self-issued certificates in IIS
what about a "sites" certificate? I just migrated from SBS 2003 to 2008 and brought across our certificate (mail1.firm.com). Every time we open Outlook 2007, we get certificate errors that makes it sound like Outlook is looking for something called "site" but finds the mail1.firm.com certificate instead.
Any thoughts?
Make sure you use the SBS trusted certificate to install the certificate. Does Outlook connect and download mail? This is most likely due to the sharepoint site being added inside Outlook to use Outlook as the offline data store for sharepoint. Did you set that up?
Great Blog and info. I almost went to GoDaddy or some other authority because of problems with Mobile 6.0 and SBS 2008. No matter what I did, couldn't get it to work. Everything worked great on SBS 2003 with same settings. With help from here I got all certificates straightened on IIS, etc. The key is the intermediate store and the certificate chain. Getting the .cer file on device wasn't enough - even though it said installed. It only went in device intermediate store. All was solved with Self-Signed by exporting the certificate in IIS with key and choosing include all certificate chains. It makes a PFX file which will download over http and install in one step on Mobile 6.0!! After that it worked immediately - no need for trusted root from a major authority. Activesync bliss again!
Running the SBS2008 "Add a trusted certificate" wizard geneates a Certificate Request which includes only 3 domains - domainname.com, remote.domainname.com and internalservername.internaldomain.local. There are no autodiscovery domains. Does SBS2008 specifically do things in the background which means these domains are not required and therefore not part of the request file? I see an additional zone for remote.domainname.com gets created by the Internet Address Wizard. We have internally connected OL2007 clients (domain connected), and OL2007 installed on a bunch of laptops that connect via a VPN (not domain connected) and don't use RPC over HTTPS / Outlook Anywhere. Should I proceed and purchase the certificate with just the 3 domains? Thanks
You would create an SRV record in your public DNS entry (godaddy for example) that points the autodiscover service to "remote".
The internet address management wizard will do this for you, just select godaddy (if that's where your domain is) and then the domain you want to use. don't bother with the godaddy transfer/purchase website, just type in your godaddy creds and it will work.
This post is very help.
However, while installing my godaddy certificate, I am stuck on the last step (Add trusted certificate using Trusted certificate Wizard).
The godaddy certificate does not show up in my wizard. Another strange thing is after importing the certificate using MMC, the trust certificate wizard seems to be reset. Instead of giving the option "I have a certificate from my certificate provider", it give the option "I want to buy a certificate from a certificate provider" as if I never submitted a CSR.
Any hints on why this is happening?
It's likely that the certificate you requested from GoDaddy doesn't match the Fully Qualified Domain Name you set up in the Internet Address Management wizard. Did you ensure you requested the exact same name from godaddy?
Dear Sean,
Does your method of using a single domain SSL certificate from godaddy still work fine in case my registrar doesn't allow me to create SRV records ?
Yes, this works. We have added multiple domain names in the certificate.
I don't get it, how could you add multiple domain names in a single domain certificate... ?
@Lucien, The method above doesn't work with a single SSL certificate as @JBrubakerjr said. If you cannot create SRV records, you will need either a "Multiple Comon Name (CN) certificate", in which to put the autodiscover.domain.com record in. So the multiple names would be "remote.domain.com" and "Autodiscover.domain.com". Then you would create the autodiscover record as a CNAME to the remote name, and things will work.
The other thing you can do is obtain a wildcard certificate which basically answers for * (or everything) on a domain name. They are more expensive than the single name certificate or multi-name certificate. Once this is installed, then create the autodiscover record again as mentioned above.
Sean
Sean,
I am sorry about the miss-information. I thought Lucien was referring to a multiple name (CN) certificate, meaning that we have installed one certificate that has multiple domain names in that same certificate.
My experience with wildcard certificates is that they are incompatible with Exchange, but work fine for the http. So if the certificates main purpose is for the owa or active-sync functionality, than the wildcard certificate does not work correctly.
I think I found a way to create a SRV record even if my current registrar doesn't allow it: change the DNS of the domain and have it managed by godaddy.
Another thing: Aren't there any other services that need their own certificate (OWA for instance) ? Or do they work with the same url (remote.domain.com) ?
That'll do it Lucien... they all use the same certificate, that's the design of SBS.
Good luck!
Sean,
Is this series of instructions still valid for SBS 2011? The wizard looks identical so I am guessing yes. Lastly, in the year since you wrote your article, when downloading the completed cert from GoDaddy, they now offer EXCHANGE as an option in addition to IIS7, IIS6, etc. Should EXCHANGE now be the selected server type over IIS7 when selecting the download?
I figure you know these by heart, so thanks in advance?
Totally still valid for SBS 2011.. enjoy!
Obviously I'm not as smart as I thought I was because I'm having problems following your instructions, or I'm being misled by GoDaddy instructions. Your instructions suggest "Since GoDaddy provided me with a file, I’m going to browse to the file (alternatively ..." but I am not offered a chance to browse for a file - what am I missing?
I'm trying to install a certificate for SBS2008, and GoDaddy instructions refer to using Import-ExchangeCertificate to bring in the .crt file I got when I applied for the certificate. (I downloaded one for IIS5.)
When I try to import the Trusted Certificate for the last step, all I can see is two Self Issued certificates.
What am I doing wrong?
Jerome
If you don't get a file, and get an encrypted string, you can also paste that into the wizard, was that where the confusion was?
I have a SBS 2011 Srv and a 2008R2 Terminal Server. Go daddy cert was installed and works internally and externally for the remote web access/web workplace.
However, I also have the Remoteapp website installed on the SBS box and users can log in and see the published applications. The issue is when they run the published apps, they get a certificate warning stating the certificate is not from a trusted certifying authority and the certificate name is servername.domainname.local instead of the name on the godaddy cert.
Anyone know how to fix this ... been reading for a few hours and nothing I have tried worked.
Thanks
Is your published app URL and your RWW URL the same? if not you need to buy a wild card certificate or make them the same
Not sure what the URL is for the Apps. To get it to work internally i had to set the RD session host to the tsserver.domain.local. I tried to use the url of the RWW, but that wouldn't work at all
FYI, if you are using RD web on a server that has Exhange or SBS you will run into authentication issues between RD Web and Exchange's OWA. Run this powershell command:
Get-OutlookAnywhere | Set-OutlookAnywhere –IISAuthenticationMethods: Basic, ntlm
This will set OWA to use NTLM instead of form based authentication for RPC, RD web has to use NTLM
http://social.technet.microsoft.com/Forums/en/winserverTS/thread/1da9cd90-80f4-4087-9edf-2d9cfa1d312f
http://social.technet.microsoft.com/Forums/en-US/winserverTS/thread/e91af0b9-19af-40e8-87b7-bea127111bc0/
http://social.technet.microsoft.com/Forums/en-US/winserverTS/thread/84ef18d6-ac63-4c83-81c0-0b0f0a0a396c
Thanks for this , Sharks at http://www.netometer.com/video/tutorials/godaddy-add-trusted-certificate-sbs-2008/step3/index.php wanting to charge for it!
One think to check is the Date and Time is correct on the server
One issue on the UCC/SAN certificate recommended or a wildcard certificate is that according to the GoDaddy representative I spoke to, the UCC/SAN certificate does not support a wildcard.
So, before generating your cert request it is critical that you can positively identify the subdomains you need or if you desire to use a wildcard. This will determine which GoDaddy certificate you will order.
I appreciate your post I purchased a Single Domain Name Certificate for my EBS setup and thought I would have to turn around and ask for a credit and upgrade to a 5 UCC SSL.
So do you see any reason why I couldn't do the same for my EBS setup as long as I can get my DNS registrar to create a SRV record? Obviously the setup will be a little different.
Also I noticed in a post that I should have the following SANs for everything to work:
mail.contoso.com
contoso.com
contoso.local
autodiscover.contoso.com
Server01.contoso.local
Server01
My main question is not having the local SANs shouldn't be a problem right? It would only be a problem for internal clients trying to access OWA or any other HTTPS website through IE since they will be proxied through Forefront TMG to gain access to them right? Sorry just want to be sure I won't mess stuff up. :)
Todd4Tech, I believe you are right on the money. no change between SBS and EBS other that what you call out.
Hi Sean, great work on the article.
I have an expired certificate from Go-Daddy. I renewed the certificate and ran into some problems.
Can I just re-key the certificate (using the add trusted certificate wizard and the re-key option in Go-Daddy) and use the remainder of the wizard to complete the process
Ive been battling with certificates for a while for a couple of our customers (installation and configuration) and found a perfect document for resolving certificate errors in outlook (if you are all interested).
http://www.shudnow.net/2007/08/10/outlook-2007-certificate-error/
Hope this helps someone.
PS. If you change your internal domain name, re-run the internet connection wizard to correct any problems and check the IIS binding as there may be 2 entries of your domain in the virtual directory (if the wizard errors out)-known from experience.
Thanks for the post, worked for SBS2011 as well btw.
Thanks, worked very well
I had remote.oldDomain.org with self-signed and then added godaddy with remote.newDomain.org.uk. Now everything is messed up and I'm getting browser cert errors for the old and 403 pages for the new. Any advice appreciated.
you'll need to install the new certificate for the new remote.newDomain.org.uk. you can do that with the domain wizard I believe in SBS 2008. it's been a while.
I have SBS2011 and now installed a separate web server in a DMZ in order to run xxx.mydomain.co.uk.
I added a SAN to the godaddy certificate, which will not install on the SBS machine. The error simply states unable to add certificate to RWA.
Any ideas anyone?
I haven't seen that one gjross. Are you using the SBS wizards, or the IIS wizards? and which version of SBS are you using, SBS 2001 essentials or standard, they are different wrt to certificates.
I used the SBS wizard to import the new certificate and this is on 2011 standard. It doesn't seem to like the fact that there is an added SAN - is this because the new certificate has a different key to the one originally created by the SBS wizard?
I had to re-key the certificate by regenerating the code from SBS and hey presto, it worked.
I have a problem trying to install a third party cert. The SBS certificate wizard seems to only generate an SSL request in 1024 bits whereas most third party SSL providers will only provide a 2048bit ssl certificate. So what is the best way to generate and complete the request so everything still works ?
You can also generate this certificate using the IIS wizards from inside the IIS management tools.
Many thanks for the detailed description.
Our company went with this solution quite a few years back, and we just renewed our cert.
GoDaddy does not allow a SAN with a local name however anymore('host.localdomain.local') and now our Outlook clients get security prompts from the Exchange server, as I had to remove the 'local' SAN from the renewed certificate.
It seems possible to fix this internally without renaming the internal 'domain', but I am not sure where to start.
Any tips or tricks would be hugely appreciated.
and Outlook cannot connect using the local server name? of just ?
It could connect, but received a security prompt which "confuses" users, so to speak.
The security prompt was only given in Outlook to a domain-user, when apparently using the auto-discover features of Exchange.
Users not a member of the internal windows domain always performed a manual configuration, and never were prompted with the mismatched certificate name.
We solved it in the end by using these instructions:
http://support.microsoft.com/kb/940726
In addition we had to create an external DNS record for the internal host, to properly resolve to an internal IP.
We didn't find it the most elegant solution, but apparently it was decided that a secure certificate should not have any SANs referring to host.localdomain.local names anymore...
We currently have our domain name registered with Network Solutions. Our SBS 2008 server is using a self-issued certificate. I like the detailed instructions on using a GoDaddy SSL certificate and would like to try this method. What "complications" can be explected if I try to obtain a certificate through GoDaddy when my registar is Network Solutions?
you'll most likely be fine getting your certificate from a different provider than your domain. We only encourage this inside of the domain wizard in 2008+ because it makes everything a little more simple.
Thanks for the tips regarding SSL certificate, I've been encountering error as I browse the internet in our home PC. It says that it's because there are disabled certificates under it and through your blog, I've come to fixed them.
Hi Sean: Thanks for the helpful post. I inherited an SBS2008 server + memb er server domain, in which a Godaddy wildcard cert had been installed on the SBS Server as well as the member servers. I renewed the wildcard cert at Godaddy by generating a new CSR on the member server (in IIS7), then re-keying the cert and installing it on the member server. It's working fine there. I then exported the cert on the member server to a PFX, and imported it into the SBS server using the certificates console. I now see the old and new wildcard certs in the "Personal" folder in the certificates console. I then tried to run the SBS wizard to "replace the existing cert" "with one already installed on the server", but the new cert doesn't appear in the window (no certs appear there). Just to be safe, I imported the intermediate certificates file as well (even though it must have already been on the server), but I still can't import the new cert (it doesn't appear)?
Hi!
I had to reinstall my SBS2011, due to some misconfiguration. The bottom line: Can I re-use the GoDaddy certifikate files I made during the first installation attempt?
Right now the wizard prompts me for a PFX-file, but I only have the intermediate and crt files from GoDaddy. I never got around (or understood) that an export to a PFX file would have been a good desicion before I began re-installation... :-(
Does this mean I have to buy a completely new certificate? Nothing else has changed (same domain, IP, server HW, etc)
@Marcin, you can have GoDaddy re-key your certificate using a new CSR generated from the rebuilt SBS certificate wizard.
Thanks for sharing this information. Lots of people who have their own websites use a Standard SSL certificate. it gives hem the look that they want on their site and assures visitors that the site is secure.
I unsuccessfully spent countless hours trying to enable ssl on my site on godaddy. I hope i had found this article earlier.
Very helpful article ! I was always curious about all these complex algorithms that are being used in these ssl encryptions.
There is absolutely no need to replace the Exchange certificate. Please don't bother doing this. Exchange certificates being self issued do not affect any functionality what-so-ever. So just use our trusted certificate wizard and you won't go a-stray.
Hi Harun,
Absolutely correct, this is only to install the IIS certificate, it doesn't touch the exchange cert, there is no need to change that one.
Post a Comment